In June, a Google Cloud Armor customer was targeted in a series of HTTPS DDoS attacks that peaked at 46 million requests per second. This is the largest Tier 7 DDoS ever reported.
Google has observed that the frequency and size of distributed denial of service (DDoS) attacks has increased exponentially in recent years. Today’s internet-facing workloads are at constant risk of attack, with impacts ranging from poor performance and user experience for legitimate users to increased operating and hosting costs and the inability to fully utilize mission-critical workloads.
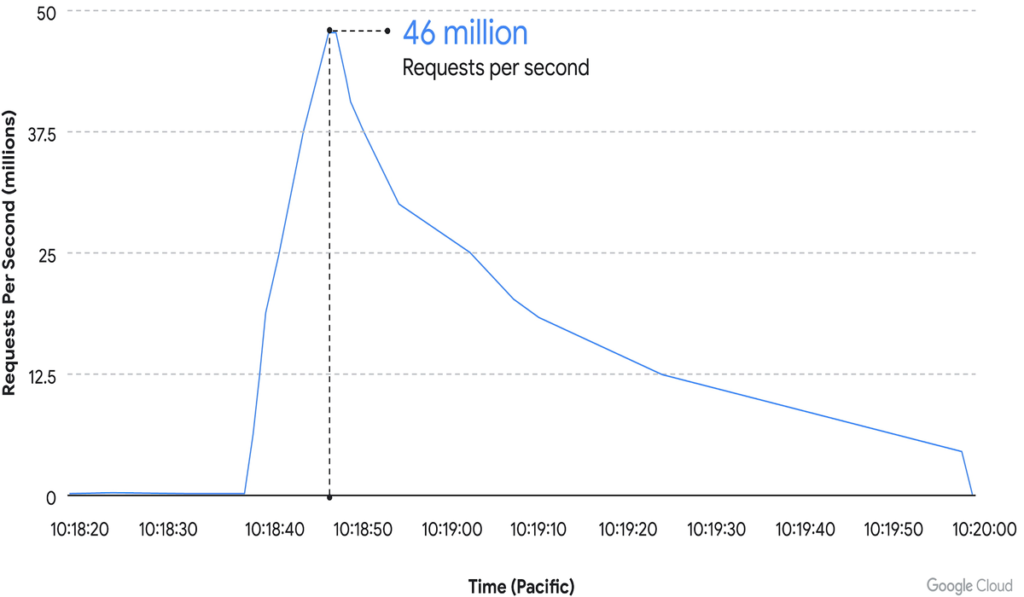
On June 1, a Google Cloud Armor customer was targeted in a series of HTTPS DDoS attacks that peaked at 46 million requests per second. This is the largest Tier 7 DDoS ever reported – at least 76% larger than the previously reported record.
To give you an idea of the scale of the attack, this is like getting all the daily requests to Wikipedia (one of the 10 most trafficked websites in the world) in just 10 seconds.
Cloud Armor Adaptive Protection was able to detect and analyze traffic early in the attack lifecycle. Cloud Armor alerted the customer with a recommended protective rule that was deployed before the attack reached its full magnitude. Cloud Armor blocked the attack by ensuring that the customer’s service stays online and continues to serve its end users.
Cyber Attacks come from 32 countries
In addition to the unexpectedly high traffic volume, the attack had other notable features. There were 5,256 source IPs from 132 countries that contributed to the cyber attack. The top 4 countries contributed about 31% of the total attack traffic.
When the attack peaked at 46 million rps (requests per second), Cloud Armor’s proposed rule was in effect to block most of the attack and ensure that targeted applications and services remained available. This enabled the attack to be eliminated immediately.

How was the attack stopped?
The attack was halted above Google’s network, and malicious data requests were blocked upstream from the client’s app. Before the attack began, the client had already configured Adaptive Protection in the corresponding Cloud Armor security policy to learn and create the basic model of normal traffic patterns for their service.
As a result, Adaptive Protection was able to detect the DDoS attack early in the event, analyze its incoming traffic, and generate an alert with a recommended protection rule before all these attacks escalate.
First visual resource: Unsplash