TRM Labs, a digital asset compliance and risk consulting firm, issued an investigation report on Discord fraud and phishing attacks in recent months on July 25, saying that with the popularity of NFT projects, Discord attracts more and more hackers, using stolen Discord accounts in a single month in June. NFT-related minting scam phishing attacks increased by 55%, costing the entire NFT community around $22 million since May.
Chainabuse, a fraud reporting platform operated by TRM Labs, has received more than 100 Discord attack reports since May.
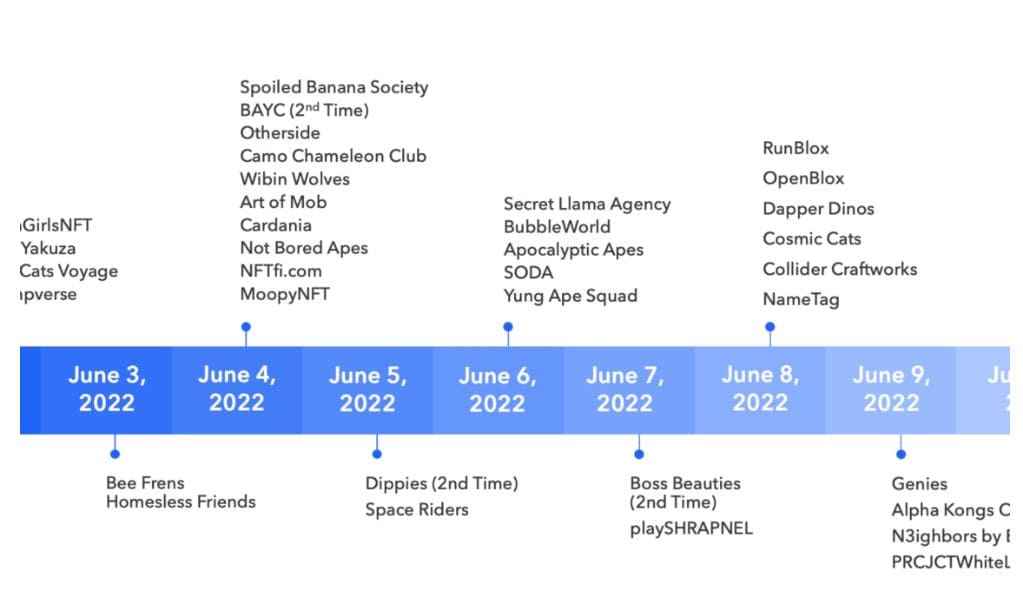
Common scams used by Discord hackers
According to TRM Labs analysis, many hackers attacking the NFT project Discord use similar scams:
Sophisticated social engineering attacks such as phishing and impersonating administrators with fraudulent accounts.
Exploiting bot vulnerabilities such as Mee6, allowing administrators to automatically assign and delete roles and send community messages.
In some cases, attackers even updated admin settings to prevent Discord moderators from interfering with hacking operations.
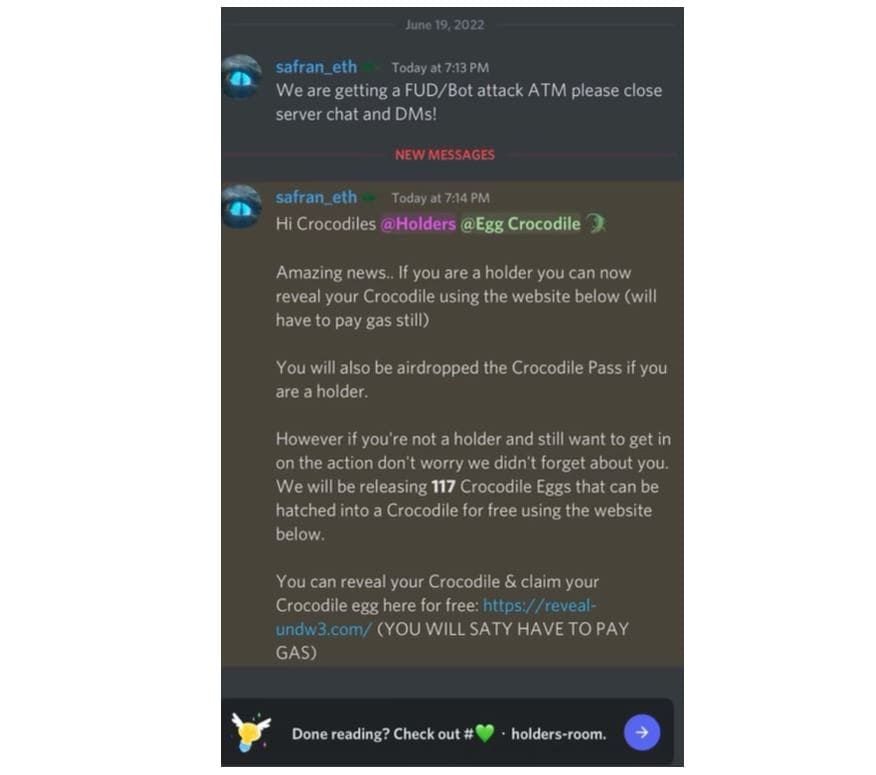
TRM Labs pointed out that hackers are trying to exploit the sense of urgency often associated with NFT minting events to prompt users to act quickly so as not to miss out on freebies or limited whitelists. Below is a phishing image of scammers enticing Discord channel members to click on a link.
For well-known projects, the source of the attack is highly relevant
The TRM Labs report also mentioned that phishing mainly attacks many well-known NFT projects such as BAYC, Bubbleworld, Parallel, Lacoste, Tasties, and Anata. The attackers deliberately promoted “BAYC, MAYC and Otherside exclusive giveaways” to users with valuable NFTs, and provided scam links that prompted users to send mint fees in ETH.
When the victim clicks on the link, the transaction hacks into the wallet and transfers the NFT to the attacker’s wallet. Unbeknownst to the victim, this sets the setApprovalForAll or similar call function for the wallet, allowing the attacker to approve the wallet to transfer the NFT to the specified wallet address. In the end, the stolen NFTs are all transferred to the wallet designated by the attacker.
TRM Labs Investigations utilizes tool to track scammer wallets related to Yuga Labs NFTs. They sold the stolen goods and distributed the proceeds of the stolen goods to three wallet addresses, and then used the money mixing platform Tornado Cash and intermediate wallets to launder the money. Three wallets were exposed in May and June. After the funds were transferred, part of them eventually flowed into one of the exchange’s wallets, which was also found to be related to the Discord leak.
The number of attackers involved is still unknown, security companies: or from within China
TRM Labs reiterated that although the investigation is active, it is difficult to know the number and shape of the prisoners due to the speed of the crime. TRM suspects that the attacks were coordinated by different hackers to execute the scam on a large scale, but have not proven the source of the attacks.
Decrypt reported that the blockchain security company Halbornpd investigated fraud incidents in recent months, and the attack security engineer boldly stated that the attack originated from China:
Our analysis points to this attack coming from a Chinese group, mainly targeting high-value users. We expect logarithmic growth in Advanced Persistent Attack (APT) activity, and we also expect to see the emergence of their own adversaries targeting Web 3.0 companies and retail customers.